Topic Covered in This Page
- Common types of phishing attacks
- What us Vishing or voice phishing?
- What us Email phishing?
- What us Pop-up phishing?
- What us Clone phishing?
- What us Website spoofing?
- What us Image phishing?
- What us Search Engine Phishing?

Any message deliberately made to seem to be from an authentic sender is referred to as phishing. Phishing is one of the most common forms of cyberattack since it can appear in emails, phone calls, and text messages, among other places. “fish hooks snagged with emoji faces”
And how can you best defend yourself? Make sure you are properly informed.
Knowing the strategies that a cybercriminal can employ against you is helpful if you want to avoid falling victim to phishing schemes.
An overview of the most popular phishing campaigns used by cybercriminals to steal your information can be seen below.
1 – Spear phishing
2 – Vishing
3 – Email phishing
4 – HTTPS
5 – Pharming
6 – Pop-up phishing
7 – Evil twin phishing
8 – Watering hole Phishing
9 – Whale
10 – Clone phishing
11 – Deceptive phishing
12 – Social Engineering
13 – Angler Phishing
14 – SMS phishing
15 – Man-in-the-middle attack
16 – Website spoofing
17 – Domain Spoofing
18 – Image phishing
19 – Search Engine Phishing
Spear phishing
Spear phishing involves targeting a specific individual in an organization to try to steal their login credentials. The attacker often first gathers information about the person before starting the attack, such as their name, position, and contact details.
Vishing or voice phishing
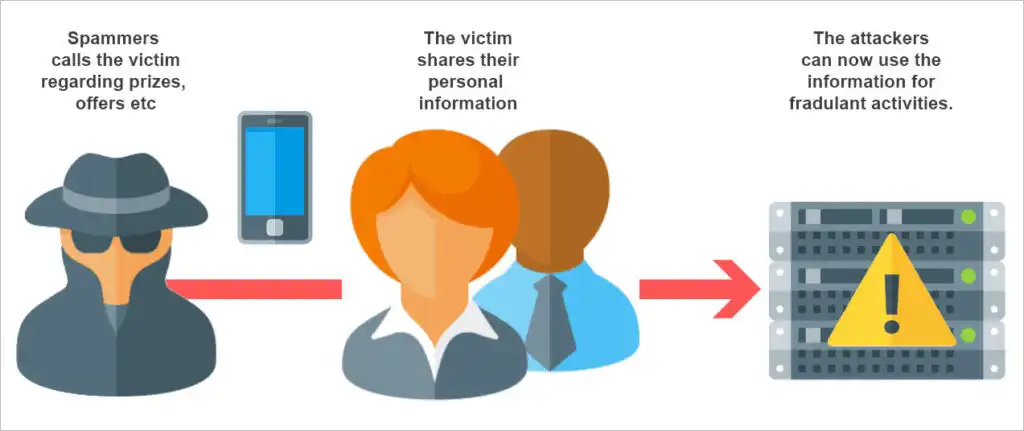
Vishing, which is short for “voice phishing,” is when someone uses the phone to try to steal information. The attacker may pretend to be a trusted friend or relative or to represent them.
Email phishing
In an email phishing scam, the attacker sends an email that looks legitimate, designed to trick the recipient into entering information in reply or on a site that the hacker can use to steal or sell their data. In one case of email phishing, Hackers used LinkedIn to grab contact information from employees at Sony and targeted them with an email phishing campaign. They got away with over 100 terabytes of data.
Protect yourself from phishing,
Read detailed information about Email Phishing.
HTTPS
An HTTPS phishing attack is carried out by sending the victim an email with a link to a fake website. The site may then be used to fool the victim into entering their private information.
Pharming
In a pharming attack, the victim gets malicious code installed on their computer. This code then sends the victim to a fake website designed to gather their login credentials. In 2007, a complex pharming attack went after at least 50 financial institutions across the world. Users were directed to false websites and instructed to enter sensitive information.
Pop-up phishing
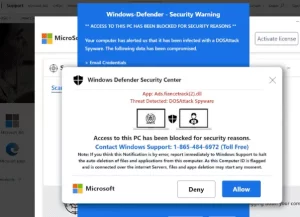
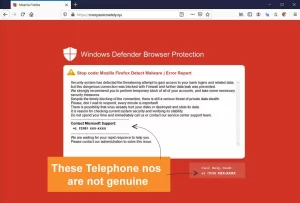
Pop-up phishing often uses a pop-up about a problem with your computer’s security or some other issue to trick you into clicking. You are then directed to download a file, which ends up being malware, or to call what is supposed to be a support center.
Users have sometimes received pop-ups saying they can qualify for Office 365 or Norton renewal, which would supposedly avail them of extended protection for their devices.
Read more details about an example of
Pup-up Phishing – Window Defender Security Scam
Evil twin phishing
In an evil twin attack, the hacker sets up a false Wi-Fi network that looks real. If someone logs in to it and enters sensitive details, the hacker captures their info.
A Russian military agency called GRU was recently charged with executing evil twin attacks using fake access points. The access points were made to look like they provided connections to real networks when in reality they led users to sites that stole their credentials or downloaded malware onto their computers.
Watering hole Phishing
In a watering hole phishing attack, a hacker figures out a site a group of users tends to visit. They then use it to infect the users’ computers in an attempt to penetrate the network.
Whale or whaling attack
A whaling attack is a phishing attack that targets a senior executive. These individuals often have deep access to sensitive areas of the network, so a successful attack can result in access to valuable info.
The founder of Levitas, an Australian hedge fund was the target of a whaling attack that led the individual to a fake connection using a fraudulent Zoom link. After following the link, they had malware installed on their system, and the company lost $800.000.
Clone phishing

A clone phishing attack involves a hacker making an identical copy of a message the recipient already received. They may include something like “resending this” and put a malicious link in the email.
Deceptive phishing
Deceptive phishers use deceptive technology to pretend they are with a real company to inform the targets they are already experiencing a cyberattack. The users then click on a malicious link, infecting their computer.
Users were sent emails that came from the address support@apple.com and had “Apple Support” in the sender information. The message claimed that the victim’s Apple ID had been blocked. They were then prompted to validate their accounts by entering information the hacker would use to crack it.
Social Engineering
Social engineering attacks pressure someone into revealing sensitive information by manipulating them psychologically.
A hacker pretended to be a representative of Chase Bank while saying that the action was needed on the target’s debit or ATM card. The attacker was trying to pressure the victim into divulging their information by leveraging their fear of not being able to access their money in their Chase account.
Angler Phishing
Anglers use fake social media posts to get people to provide login info or download malware.
Hackers pretended to represent Domino’s Pizza on Twitter, fielding the concerns and comments of customers. Once they engaged with a customer, they would use their situation to try to get their personal information—using the guise of trying to get them a refund or a reward.
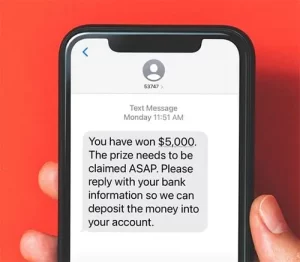
SMS phishing or Smishing
Smishing is phishing through some form of a text message or SMS.
Hackers pretended to be from American Express and sent text messages to their victims telling them they needed to tend to their accounts. The message said it was urgent, and if the victim clicked, they would be taken to a fake site where they would enter their personal information.
Man-in-the-middle attack
With a man-in-the-middle attack, the hacker gets in “the middle” of two parties and tries to steal information exchanged between them, such as account credentials.
Example of Man-in-the-Middle-Attack
In 2017, Equifax, the popular credit score company, was targeted by man-in-the-middle attacks that victimized users who used the Equifax app without using HTTPS, which is a secure way to browse the internet. As the users accessed their accounts, the hackers intercepted their transmissions, stealing their login credentials.
Website spoofing
With website spoofing, a hacker creates a fake website that looks legitimate. When you use the site to log in to an account, your info is collected by the attacker.
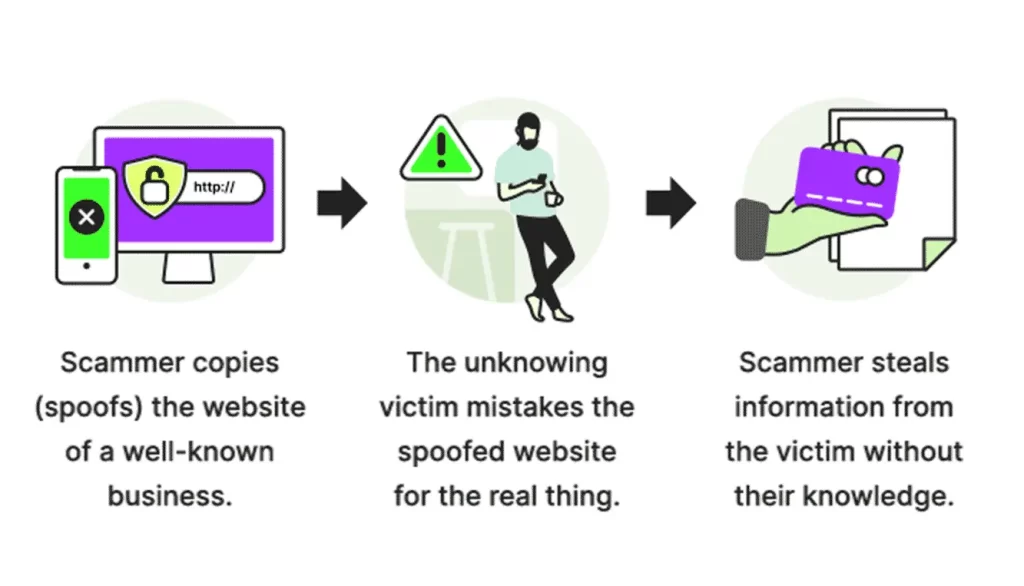
Hackers made a fake Amazon website that looked nearly identical to the real Amazon.com but had a different Uniform Resource Locator (URL). All other details, including fonts and images, looked legitimate. Attackers were hoping that users would put in their username and password.
Domain Spoofing
Domain spoofing, also referred to as DNS spoofing, is when a hacker imitates the domain of a company—either using email or a fake website—to lure people into entering sensitive information. To prevent domain spoofing, you should double-check the source of every link and email.
An attacker would execute a domain spoofing attack by creating a fraudulent domain made to look like a real LinkedIn site, for example. When users enter the site and enter any information, it is sent straight to hackers who could use it or sell it to someone else.
Image phishing
Image phishing uses images with malicious files in them meant to help a hacker steal your account info or infect your computer.
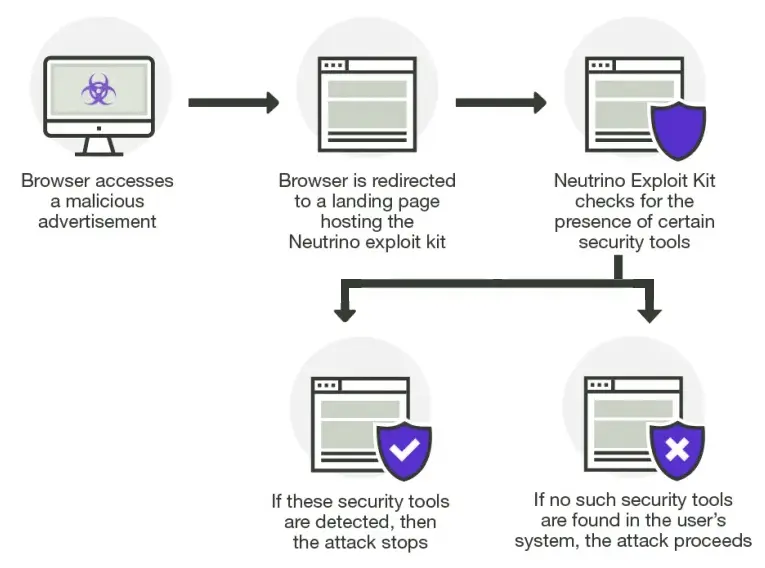
Hackers have made use of AdGholas to hide malicious code written in JavaScript inside images and HTML files. When someone clicked on an image generated by AdGholas, malware would be downloaded onto their computer that could be used to phish for their personal information.
Search Engine Phishing
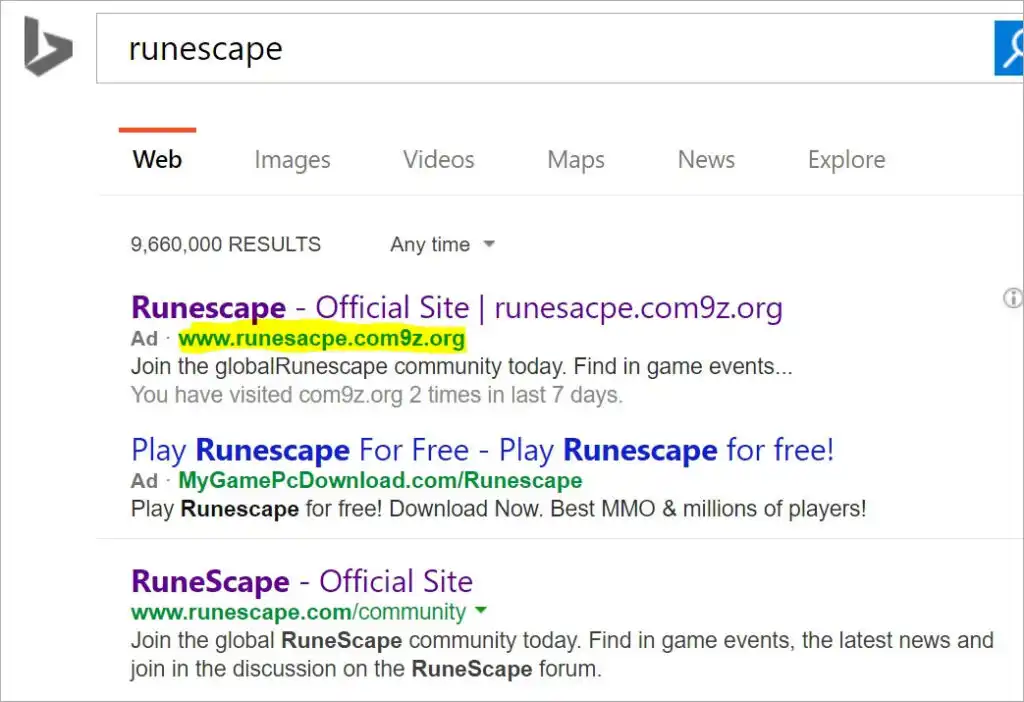
Read More about search engine phishing
A search engine phishing attack involves an attacker making fake products that look attractive. When these pop up in a search engine, the target is asked to enter sensitive information before purchasing, which then goes to a hacker.

This article is about Phishing, How to identify and protect yourself from different types of phishing. If you are facing any security issues with your PC & laptop, call us for assistance. Our service engineer will certainly guide you. You can also ask for a free PC Diagnostic Service



