Topic Covered in This Page
- What Are the Different Types of Phishing?
- Phishing Detection with Popular Search Engines
- What is Phishing and How Does it Work?
- A malicious search engine attack
- Phishing Attack using a Search Engine
- What is Phishing and How Does It Work?

When hackers employ search engine optimization to rank among the top results on a search engine in an effort to direct users to a fake website, the practice is known as search engine phishing, often referred to as SEO poisoning.
The fake website is designed to look authentic so that users who click on it continue to log into their accounts as usual. They are unaware that if they reuse their passwords, crooks will be able to acquire their login information and use it to compromise their account or a number of accounts.
Anyone might fall victim to the fraud known as search engine phishing. It’s crucial to understand how it operates and what one may do to protect themselves from falling for this particular phishing scam.
What is a Search Engine?
Anyone can use a search engine as a tool to conduct online information searches. Search engines like Google, Yahoo!, DuckDuckGo, and Bing are among the most widely used. Search engine optimization is used by cybercriminals to attract more potential victims into their scams because so many people use search engines on a daily basis.
What is Search engine optimization?
The technique of increasing a site’s exposure on search engines is known as search engine optimization (SEO). Searchers are more likely to click and find a site that has better search visibility. As a result, there are more people visiting the website, which increases the likelihood that they will become clients or loyal customers.
How Does Search Engine Phishing Work?
Search Engine Phishing begins with a search. We immediately visit our preferred search engine and type the term into the search box if we need to find something online. The page that displays the results is referred to as the search engine results page (SERP) or simply “search results.” It’s significant to remember that, in terms of search results, only 0.63% of users click through to Google’s second page when looking for something. Therefore, for businesses to be clicked on, they must be included on the top page.
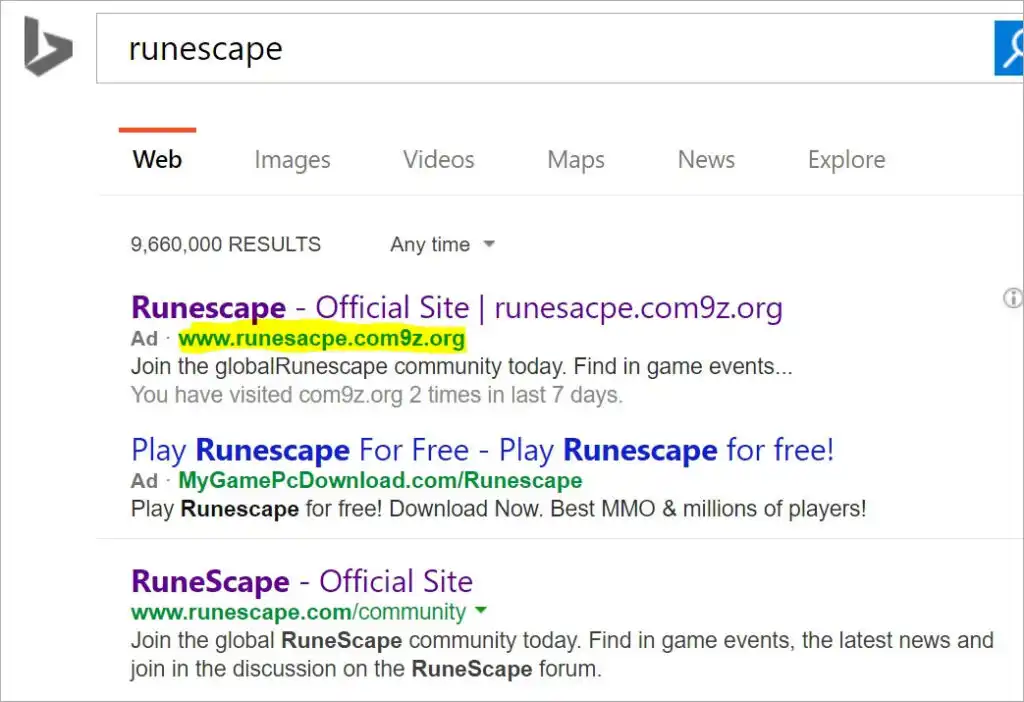
Cybercriminals can use SEO to improve their search engine rankings and draw more attention to their fake websites from users. Even though we rely on search engines to provide us with the most reliable and beneficial information, fraudsters will inevitably try to con us.
We could not even be aware that we are on a faked site using search engine phishing until it is too late. There are, nevertheless, a few warning indicators that can help you identify a faked website. Some indicators are:
- Random pop-up windows
- Your equipment is too hot
- Your gadget is operating more slowly than usual.
- grammatical and/or spelling mistakes
- A strange-looking URL
How to Prevent Phishing on Search Engines
Here are a few ways you may guard yourself against falling for search engine phishing scams.
Before clicking on a search result, verify the URL.
The website address, also known as the entire URL, of the site you’ll be taken to when searching online is always displayed in the search results. Even though a site is listed in search results, it’s crucial to always check the URL before clicking because you can find that anything is wrong. The spoof URL may resemble Chasee.com if the site is pretending to be a bank like Chase.
Another way you can double-check a site’s URL is by using Google
Simply right-click a search result and choose “copy link address” from the dropdown menu. Once copied, you may put it into the tool to find out whether the website is safe to visit. The tool will alert you if something is unsafe, and you shouldn’t click on the search result.
Purchase a password manager.
An instrument called a password manager helps users create, manage, and securely save their passwords. The only password they need to remember is their master password if they use a password manager. Many password manager programs provide an autofill function to simplify users’ account login processes.
The fact that a password manager won’t automatically fill in your login information if the website address doesn’t match the one recorded in the record in your vault is one of its little-known advantages. This can stop you from entering your login information at all and guard against account compromise.
Purchase a tool that notifies you if a search result is risky.
Based on the URL and content of the page, there are tools that can tell you whether or not it is safe to click on a search result. One tool is Geekway Pro Safeguard, which indicates whether a search result is safe to click on by placing a green check mark next to it. A red flag warning shows to the right of the search result whenever the tool determines that a site might be hazardous.
How to respond if you are a victim of Search Engine Phishing
Sometimes people visit the website and submit their credentials before realizing they’ve been the victim of search engine phishing. Here are some actions you can do to decrease the impact if this occurs to you.
Launch antivirus and anti-malware programs
Due to the fact that search engines are a tool that we all use on a regular basis, it’s probable that you or someone you know will become a victim of this kind of phishing scam. If you do, running antivirus and anti-malware software on your device is one of the most crucial actions you must take. It’s critical that you take action to delete any malware that might have been unintentionally installed when you were visiting a spoof site.
immediately change your password
You should reset your password as soon as you know you entered your credentials into a phished website. If you don’t, online criminals might gain access to your account. Depending on the account they infiltrate, they may cause significant harm or even steal your money.
Password managers streamline the process of organizing and remembering your passwords and make the transition to strong, one-of-a-kind passwords easy.
Search engine phishing is one example of the lengths cybercriminals will go to in order to deceive people into falling for their frauds. Phishing attacks continue to become more sophisticated. Learning about them is a good first step, but being watchful for phishing schemes is equally crucial. Find out more about typical phishing attack types and how to prevent them.

This article is for Search Engine Phishing. If you are facing any issues with windows security & Phishing attack, call us for assistance. Our service engineer will certainly guide you. You can also ask for a free PC Diagnostic Service



